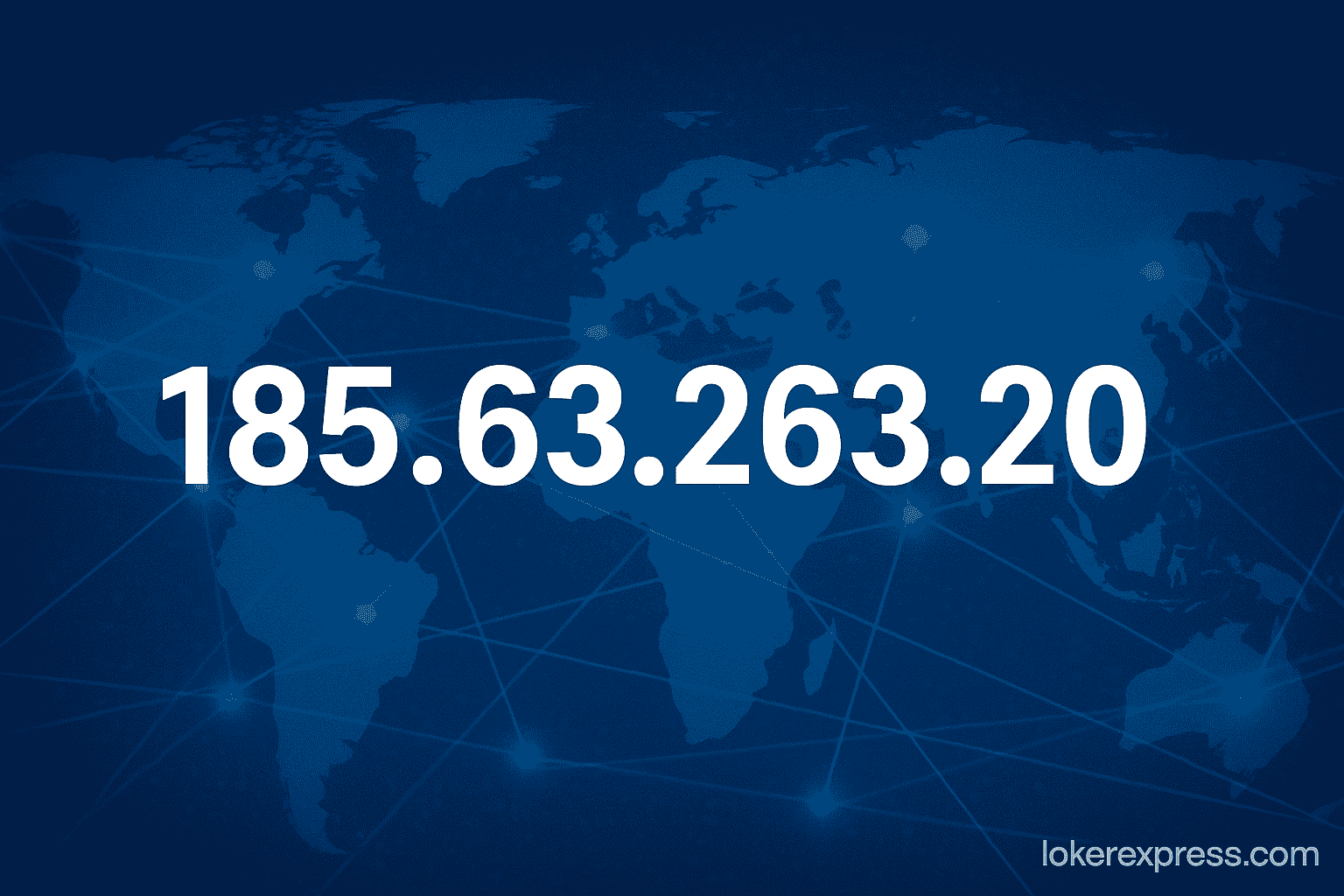
Introduction: Why IP Addresses Matter in the Digital World
In today’s digital ecosystem, IP (Internet Protocol) addresses are the backbone of connectivity. Every device, from your smartphone to enterprise-level servers, relies on these numerical identifiers to communicate across the internet. But not all IP addresses are created equal. Some are active and legitimate, while others raise eyebrows—either due to structural irregularities or mysterious appearances in logs, forums, and security analyses.
One such puzzling entity is 185.63.263.20. At first glance, it appears like any other IPv4 address. However, upon closer inspection, several issues arise—especially with the format and technical validity of this IP. This article offers a comprehensive analysis of 185.63.263.20: its format, implications, potential origins, and presence across the web.
Understanding IPv4 and the Technical Makeup of an IP Address
Before we analyze the nature of 185.63.263.20, it’s essential to understand what makes an IP address valid or invalid.
IPv4 addresses are composed of four octets, separated by periods, each ranging from 0 to 255. This format allows for around 4.3 billion unique combinations, enough to sustain internet traffic for several decades (although IPv6 is now emerging as a long-term solution).
Key Attributes of a Valid IPv4 Address:
- Four numerical blocks (e.g., 192.168.1.1)
- Each block is within the range of 0–255
- Follows a consistent structure with period separation
With this in mind, let’s examine 185.63.263.20.
Why 185.63.263.20 Is an Invalid IP Address
At first glance, 185.63.263.20 seems legitimate—structured correctly with four octets. But the issue lies in the third octet, 263, which exceeds the allowable range of 0–255. This makes it technically invalid according to IPv4 standards.
Implications of Invalidity:
- Cannot be used in legitimate DNS or routing configurations
- Will be rejected by firewalls and routers that enforce standard validation
- Cannot be resolved through traditional DNS lookups
So, why does such an IP still show up in digital forensics, forums, and logs?
Possible Reasons Behind the Appearance of 185.63.263.20
Although invalid, IPs like 185.63.263.20 often crop up in cybersecurity investigations, botnet logs, error reports, and fake traffic signatures. Let’s explore a few reasons why.
1. Human Error or Typo
Many users, system administrators, or developers might simply mistype a valid IP like 185.63.253.20. This small oversight can propagate across documents or codebases without being corrected.
2. Placeholder IP for Testing
Sometimes developers use obviously invalid IPs to test form validation or placeholder content. This ensures there’s no accidental connection to real-world systems during development.
3. Obfuscation by Malicious Actors
Hackers and malicious bots often inject malformed IPs into logs or communications to throw off tracking tools and confuse analysis. An invalid IP like 185.63.263.20 might serve as noise in a traffic pattern.
4. Corrupted Log Files
Data corruption in log entries—caused by software bugs or transmission errors—can create malformed IPs, including entries like 185.63.263.20.
Cybersecurity Relevance: What It Means When You See This IP
For cybersecurity professionals, the appearance of 185.63.263.20 in a log file is often a red flag—not necessarily of an attack, but of an irregularity. Whether it’s a failed spoofing attempt or simply malformed data, it requires attention.
Possible Security Scenarios:
- Spoofing Attempt: Some attackers insert fake IPs to mask their location.
- Log Pollution: Invalid IPs may dilute meaningful data in SIEM (Security Information and Event Management) systems.
- Reconnaissance Tactics: Bots may use malformed IPs to test firewall or server responses.
In essence, while 185.63.263.20 is not a threat by itself, its presence can be symptomatic of more extensive problems—like poor input validation, or an ongoing probing attempt by external sources.
How to Analyze IPs Like 185.63.263.20
When dealing with suspicious or malformed IPs, security teams and analysts should follow structured steps to interpret their origins and impact.
Step-by-Step Analysis:
- Validation Check:
Use tools likeipcalc,whois, ordigto see if the IP is formally valid or resolvable. - Contextual Log Review:
Review the logs or systems where the IP appeared. Was it in a login attempt? Network scan? Email header? - Threat Intelligence Correlation:
Check if the IP has ever been associated with known malware, botnets, or abuse databases—even if malformed. - Network Configuration Audit:
Ensure your systems validate IP formats properly and are not logging corrupt entries unnecessarily. - Alerting and Logging Tuning:
Exclude or flag invalid IPs to avoid polluting alerts and dashboards.
The Role of WHOIS and Geolocation in IP Tracing
Ordinarily, when encountering a suspicious IP, one might run a WHOIS lookup or geolocation analysis to identify the ISP, country of origin, and ASN (Autonomous System Number). However, with invalid IPs like 185.63.263.20, this approach hits a dead end.
What WHOIS Would Return:
- Likely an error or null response
- Possibly defaults to the closest valid block, such as 185.63.0.0/16
- No useful metadata
This reinforces the importance of IP format validation before attempting any geolocation or reputation lookup.
How Invalid IPs Can Mislead Businesses and Tools
From analytics dashboards to firewall logs, most business IT tools depend on accurate IP logging for:
- User segmentation
- Geo-distribution maps
- Access controls
- Threat detection
An IP like 185.63.263.20 can easily:
- Cause parsing errors
- Disrupt tracking systems
- Generate false positives or anomalies
- Affect data integrity in analytic models
Hence, businesses must ensure their input validation and data pipelines handle edge cases and sanitize IP entries effectively.
Preventive Measures: Guarding Your Network Against Anomalous IPs
To safeguard your system from malformed data and misuse, follow these best practices:
1. Strict Input Validation
Before storing or processing IP addresses, validate against IPv4/IPv6 formats using regex or IP parsing libraries.
2. Enable Application-Level Firewalls
Deploy WAFs (Web Application Firewalls) that can detect and reject malformed inputs, including suspicious IPs.
3. Log Scrubbing
Before long-term storage or analysis, scrub logs to remove or flag invalid entries.
4. Anomaly Detection
Train your SIEM or ML-based anomaly detection systems to identify malformed IPs as unusual patterns.
Read More: 185.63.253.300 – Everything You Need to Know About This IP Address
Conclusion: The Curious Case of 185.63.263.20
While 185.63.263.20 does not point to a legitimate machine or location on the internet, its existence raises important considerations in network hygiene, security analytics, and data integrity. Whether it’s a result of a typo, a security tactic, or a misconfigured system, the presence of such IPs should prompt both curiosity and caution.
By understanding and preparing for such anomalies, you can fortify your network’s defenses, enhance your monitoring tools, and ensure your data systems remain robust, accurate, and resilient.